Did you know that you can protect your important resources in Oracle Cloud Infrastructure (OCI) by using resource locking? It works just like resource locking in Azure and helps prevent accidental deletion or modification of your resources. Resource locking in OCI can be achieved by implementing a combination of Policies and Tags.
In this blog, I have explained how you can do resource locking for network resources in OCI. First, you need to create a group called “abkot-network-manager” that includes all the users who will manage the network resources in OCI.
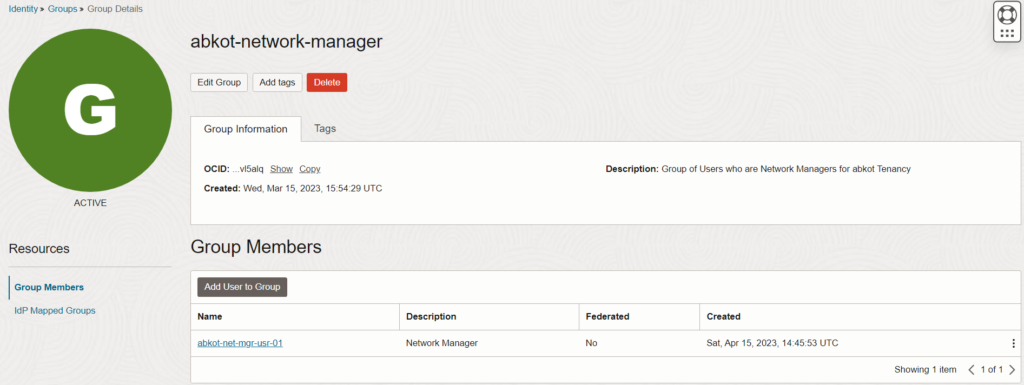
For testing purposes, I have added user “abkot-net-mgr-usr-01” to the group.
I have defined the policies of the “abkot-network-manager” group. I have created a policy “abkot-network-manager-pol” with the below policy statements:
Allow group abkot-network-manager to manage vcns in tenancy where request.permission != 'VCN_DELETE'
Allow group abkot-network-manager to manage subnets in tenancy where request.permission != 'SUBNET_DELETE'
Allow group abkot-network-manager to manage route-tables in tenancy where request.permission != 'ROUTE_TABLE_DELETE'
Allow group abkot-network-manager to manage network-security-groups in tenancy where request.permission != 'NETWORK_SECURITY_GROUP_DELETE'
Allow group abkot-network-manager to manage security-lists in tenancy where request.permission != 'SECURITY_LIST_DELETE'
Allow group abkot-network-manager to manage dhcp-options in tenancy where request.permission != 'DHCP_DELETE'
Allow group abkot-network-manager to manage private-ips in tenancy where request.permission != 'PRIVATE_IP_DELETE'
Allow group abkot-network-manager to manage public-ips in tenancy where request.permission != 'PUBLIC_IP_DELETE'
Allow group abkot-network-manager to manage byoiprange in tenancy where request.permission != 'BYOIP_RANGE_DELETE'
Allow group abkot-network-manager to manage publicippool in tenancy where request.permission != 'PUBLIC_IP_POOL_DELETE'
Allow group abkot-network-manager to manage ipv6s in tenancy where request.permission != 'IPV6_DELETE'
Allow group abkot-network-manager to manage internet-gateways in tenancy where request.permission != 'INTERNET_GATEWAY_DELETE'
Allow group abkot-network-manager to manage nat-gateways in tenancy where request.permission != 'NAT_GATEWAY_DELETE'
Allow group abkot-network-manager to manage service-gateways in tenancy where request.permission != 'SERVICE_GATEWAY_DELETE'
Allow group abkot-network-manager to manage local-peering-gateways in tenancy where request.permission != 'LOCAL_PEERING_GATEWAY_DELETE'
Allow group abkot-network-manager to manage remote-peering-connections in tenancy where request.permission != 'REMOTE_PEERING_CONNECTION_DELETE'
Allow group abkot-network-manager to manage drg-object in tenancy where request.permission != 'DRG_DELETE'
Allow group abkot-network-manager to manage drg-route-tables in tenancy where request.permission != 'DRG_ROUTE_TABLE_DELETE'
Allow group abkot-network-manager to manage drg-route-distributions in tenancy where request.permission != 'DRG_ROUTE_DISTRIBUTION_DELETE'
Allow group abkot-network-manager to manage cpes in tenancy where request.permission != 'CPE_DELETE'
Allow group abkot-network-manager to manage ipsec-connections in tenancy where request.permission != 'IPSEC_CONNECTION_DELETE'
Allow group abkot-network-manager to manage cross-connects in tenancy where request.permission != 'CROSS_CONNECT_DELETE'
Allow group abkot-network-manager to manage cross-connect-groups in tenancy where request.permission != 'CROSS_CONNECT_GROUP_DELETE'
Allow group abkot-network-manager to manage virtual-circuits in tenancy where request.permission != 'VIRTUAL_CIRCUIT_DELETE'
Allow group abkot-network-manager to manage vnics in tenancy where request.permission != 'VNIC_DELETE'
Allow group abkot-network-manager to manage vlans in tenancy where request.permission != 'VLAN_DELETE'
Allow group abkot-network-manager to manage virtual-network-family in tenancy where target.resource.tag.abkot-operation.Lock = 'No'I have created the Tag called “Lock” with the list of values “Yes”, and “No”. By adding this tag to a VCN and setting its value to “Yes”, you can prevent users from deleting or modifying that resource, even if they have the necessary permissions.
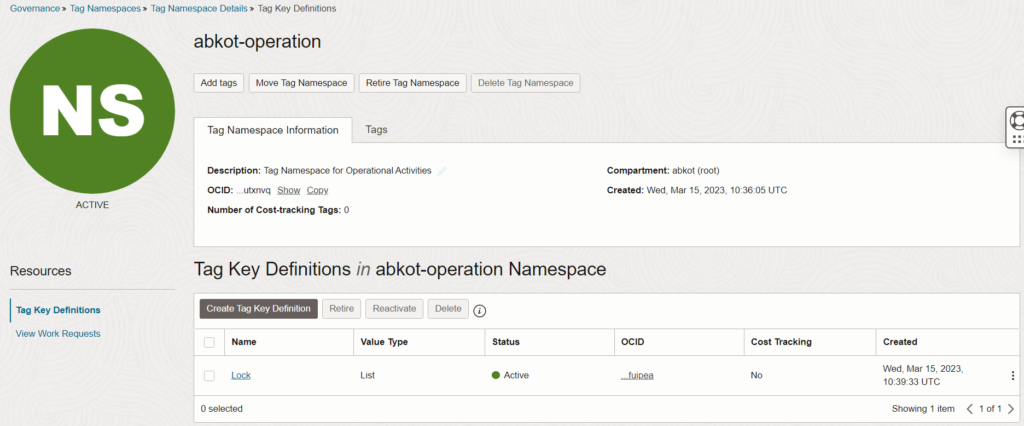
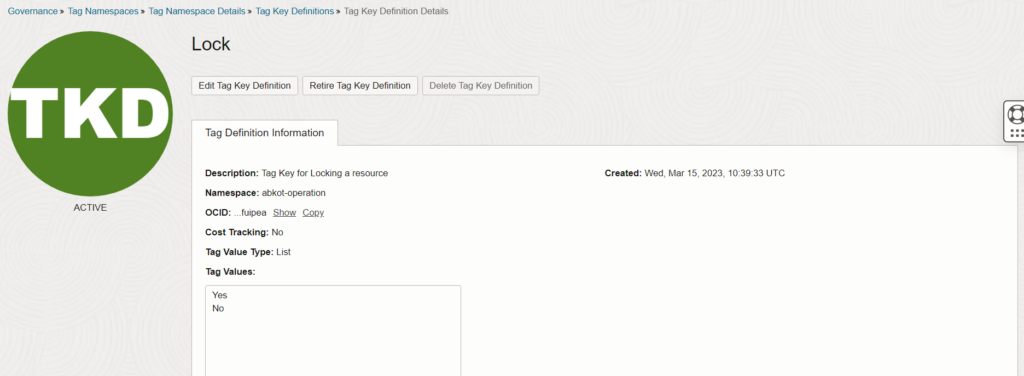
I have created a VCN “abkot-test-vcn-01″ and applied Tag “Lock” with the value “Yes”.
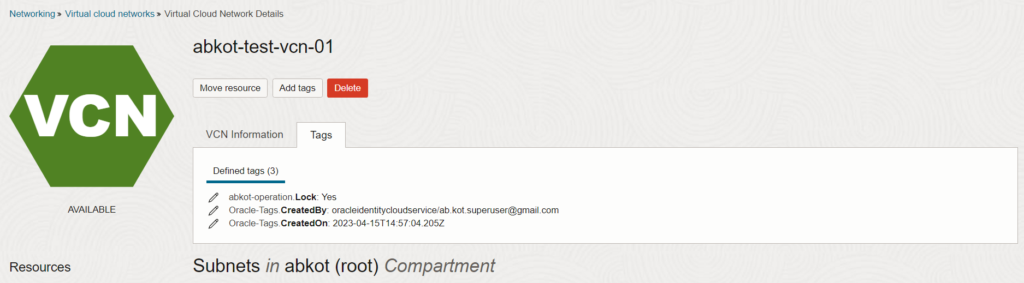
I tried deleting the VCN “abkot-test-vcn-01″ by login into user “abkot-net-mgr-usr-01” and got an error.
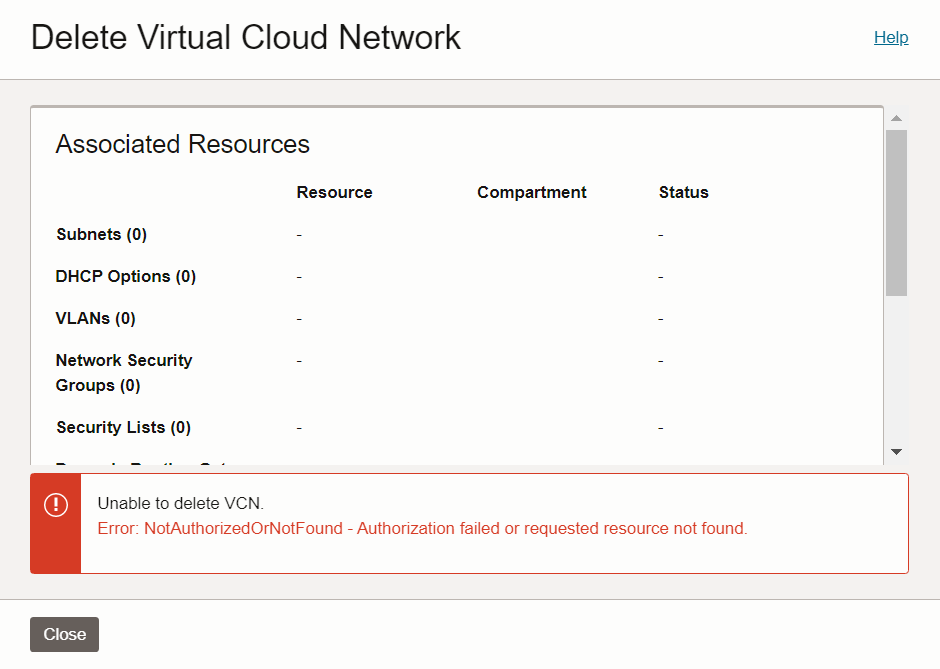
I tied changing the value of Tag “Lock” to “No“, but again got an error.
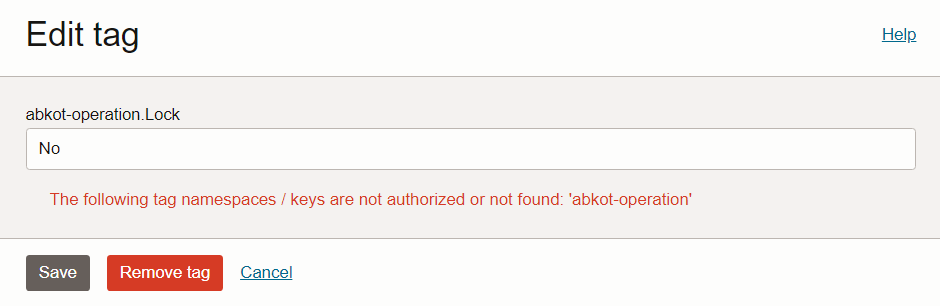
To summarize, OCI allows resource locking through Policies and Tags, similar to Azure. It provides an effective way to control resource access and prevent accidental deletion or modification.